With more than 1,800 cases of data breaches in the U.S. costing companies an average of $9.44 million per breach in 2022, passing vendor security reviews is key to winning trust and closing deals with prospects.
But even for vendors with strong security posture and all their ducks in a row, the process of passing a vendor risk assessment is daunting and time-intensive—especially when sales and revenue leaders have so many other aspects of the vendor-prospect relationship to manage to close the deal.
When sales teams feel under the gun, this can counter-productively lead them to go through the vendor risk assessment process on autopilot, seriously jeopardizing their chance of passing the review and potentially damaging their reputation in the marketplace.
For smaller startups with ambitions of moving upmarket to enterprise buyers, being able to build trust with a solid track record of delivering thorough responses to assessment requests and proactive partnership will show your viability as a vendor.
In this guide, we’ll help demystify the vendor security review process so your sales team can better partner with your internal IT and security teams to deliver faster responses to risk assessment requests—so you can ultimately close more deals, faster.
Want to get ahead on your revenue org’s next security review by managing the entire process from one single hub?
With Dock Security Profiles, you can—and later on in this guide, we’ll explain exactly how to use a shared collaborative workspace to move security reviews along at a faster pace while increasing the confidence of the evaluating party.
What is a vendor risk assessment?
A vendor risk assessment—also known as a vendor risk review or vendor security review—is a process by which companies evaluate current and potential vulnerabilities, hazards, and common attack vectors associated with using a third-party vendor’s product.
Companies conduct risk assessments as part of the due diligence process to reduce their own risk and liability should a vendor be responsible for leaking sensitive customer data or other proprietary information.
The most common areas of potential risk companies will be digging into in their security review include:
- The accuracy and availability of your information on operational, customer, and financial policies
- The capabilities, credentials, and responsibilities of your security and IT personnel, and the level of access other employees at your company have to sensitive data
- Your history with security breaches (if any) and your plans for preventing future incidents
- Your level of compliance with legal regulations and industry-standard certifications
Beyond simply maintaining a strong security posture and being legally compliant, nailing your vendor risk assessments as a vendor is also about communicating that you take security seriously—and broadcasting to future prospect companies that they can confidently do business with you.
The reality is startups have a de facto reputation for not taking security seriously, and the security review process is your opportunity to definitively put that concern to bed.
Being forthright, thorough, and easy to work with as a vendor sales team is critical to building a solid foundation for productive relationships with your customers.
Vendor risk assessments can happen at any time before and during a relationship with a customer or a prospect. A security review might be scheduled on a recurring annual or bi-annual basis, or be triggered by a trending security risk or recent incident at another enterprise that has gained global attention.
For the purposes of this guide, we’ll focus on the security review that happens during the sales process as you are being evaluated—but all these tips still apply for ongoing security reviews and audits.
Why have vendor risk assessments become so common?
To understand the vendor security assessments are becoming increasingly common, it helps to understand just how much pressures companies are under:
- In the five years since General Data Protection Regulation (GDPR) went into full effect with strict definitions, requirements and penalties around data protection, companies have had to be more rigorous and strict about security practices. Add in CCPA, HIPAA, and SOC 2, and you have a complex compliance landscape. For most companies, it’s not a matter of if but when they will experience a breach—no matter how much effort they invest in prevention.
- In a recent Whistic survey of security professionals, 81% of respondents who had experienced a security breach attributed it to vulnerability in one of their third-party vendors. Smart companies must evaluate a potential vendor from a stance of “vulnerable until proven compliant.” Sales teams need to be both empathetic and supportive of this instead of treating the assessment process as adversarial or pointless red tape.
- With the average cost of a data breach in 2022 sitting at $4.35 million—it’s in the best interest of everyone involved in the vendor risk assessment to minimize the potential for damage as much as possible.
It may seem obvious to state that companies want to minimize risk, but it’s important to remember as a vendor just how much trust your customers are putting in you to handle their data safely.
However much of a headache the review process might seem to you, your customer is going through this process with potentially dozens of different vendors—meaning dozens of vectors for attack.
But with all this work required to demonstrate a solid security posture, there is a payoff:
For small teams working to land large enterprise customers, it might feel like you’re out of your weight class throughout the entire sales process. Nailing the security review is one of the highest-leverage things you can do to punch above your weight and show that you are legitimate and trustworthy and can be taken seriously.
If you want land deals with larger companies, the easiest way to start is by treating your security practice like you would if you were a larger company.
Challenges of vendor risk assessments for sales teams
When handled poorly as a vendor, a security risk assessment can grind your sales cycle to a halt.
One report found that every clarifying request made by a potential customer (on top of the original vendor risk assessment itself) adds an additional four days to the sales cycle.
Why are they such a pain point?
- They’re hard to understand: Sales and revenue orgs don’t have as deep an understanding of super technical considerations or terminology as IT or security teams have. This can make it difficult to pass critical information without a close partnership with your IT team.
- Collaborating with stakeholders is clunky: If the sales team alone is taking ownership of passing information, requests, and clarifications back and forth between their own team and the team conducting the assessment, there’s a good chance context will get lost along the way.
- Managing documentation is difficult: Without a centralized hub for tracking important documentation and your customer’s status in reviewing the information you sent them, details will fall through the cracks. Passing important documentation about your security and privacy policies, certifications, backstops, agreements, and employee policies only over email or static docs is inefficient and makes it hard to know where you are in the process.
- Assessments are time-consuming: IT teams are notoriously pulled in several different directions, and with the average vendor spending upwards of 23 hours per week responding to risk assessment requests, it can quickly become an administrative strain on your IT team to chase down critical security information.
There’s a reason security reviews can be one of the most nerve-wracking and time-intensive parts of the sales process.
What to expect during a vendor risk assessment
Have you ever applied for a job you knew you were qualified for—only to botch the interview due to performance anxiety, lack of preparation, or failing to appropriately speak to your abilities?
A vendor risk assessment functions similarly to a job interview in that your ability to speak to your qualifications and answer questions is arguably just as important as your qualifications themselves. When it comes to building trust and confidence, the optics matter.
Another thing that both good job interviewers and vendors do to reduce the risk of failing is putting themselves in the shoes of the person who will be evaluating them by asking questions like:
- “Based on how I plan to present myself, what areas will most stand out as skill or credential gaps?”
- “Of the areas I’m being evaluated on, which will inspire confidence, and which ones will cause them to pause?”
- “What weaknesses are fixable and which are deal-breakers?”
- “Are there any questions I’m nervous about them asking?”
Your answers to these questions will tell you a lot about how prepared you are—and when you do this exercise as a part of the vendor risk assessment, you can reverse engineer an action plan by proactively fortifying any areas where red flags would be raised.
A typical security review might cover hundreds of questions, depending on the size of the prospective customer, how large the deal is, and their unique policies and thresholds for risk tolerance.
Many will be a simple yes/no answer or a box to check, and we won’t cover all of those here, but here are examples of some of the categories you can expect a review to cover—along with some information you should expect to provide:
Data security
While this category will naturally overarch the entire review process, it’s important to know the nitty-gritty of just how data is handled at your company.
You can expect questions like:
- Describe the physical security measures in place at the facilities where you store or process client data
- What type of data will be collected, shared, or stored in your application?
- What is your data retention policy during normal use?
- What is your data deletion timeline upon account termination?
Certifications and legal compliance
While “not breaking the law” is a good place to start, you should be clearing a much higher bar in order to instill confidence that you will be a reliable steward of your client’s data in the long term.
Adopting widely accepted security standards and being fluent in what these standards require will also save you time from having to answer potentially more questions during your assessment process.
Some common certifications and regulations to know are:
- General Data Protection Regulation (GDPR): One of the most strict security laws in the world that applies to any company doing business with customers related to the European Union, GDPR covers a variety of data protection principles. This includes requiring companies to minimize the amount of data collected, use it only for explicitly consented-to purposes, and process that information securely (such as with encryption), as well as a strong recommendation to appoint a Data Protection Officer (DPO) for your organization—among many, many other regulations, which you can read in full here.
- California Consumer Privacy Act (CCPA): Covering similar ground as GDPR, CCPA also grants consumers the right to correct inaccurate information businesses may be maintaining about them, and limits the use of sensitive personal information for businesses subject to CCPA.
- SOC 2: This report (which is short for Security Organization Controls) is conducted by outside auditors and provides an evaluation of the design and effectiveness of the controls used to protect customer data.
While you don’t have to be perfectly fluent in all of these certifications yourself (that’s the job of your legal, IT, and security teams), it can be helpful to familiarize yourself with them so you can enter security review meetings and discussions better informed.
You can also check out Dock’s own legal center for an example of how to make compliance and security policies transparent and available.
Staffing and personnel
The evaluating party in a vendor security review will want to ensure you have the personnel in place to make sure data and privacy is a long-term priority—and that your partnership will be a successful one.
This might include, but is certainly not limited to, making sure you have the following roles well-established:
- Data protection officer: Where does the buck stop at your organization when it comes to compliance?
- Security team: How is the security team structured? Does the reporting flow make sense? Is your security team well-diversified and sufficiently specialized in key areas (with engineers, penetration testers, etc.)? Does the team have all the appropriate personal credentials and years of experience?
- Customer support: This might not seem immediately relevant to a discussion around security, but your customer support team is going to be on the front line of data requests, account deactivations, and support tickets. Demonstrating sufficient customer support staffing shows prospects you take security seriously across the entire life of the customer relationship, not just up till the point of closing the deal.
Tools and capabilities
Making sure your employees have the skills, training, and tools necessary to actually sustain a secure, functional product is crucial. Evaluating parties will also want to ensure your product can capably sustain heavy usage and have an understanding of the customer-facing tools for securing data.
You can expect to be asked:
- What virus detection and prevention software do you use?
- Do you support multi-factor authentication (MFA) and single sign-on (SSO) capabilities—and if so, do you use third-party vendors to provide these capabilities?
- What is the service level agreement (SLA) around service uptime, and what penalties and credits exist in situations where the SLA is not met?
- Is there security awareness training in place for new hires and contractors at your company, and how often are they required to do this training?
- How do you train staff on the care and handling of personal data, information, and cybersecurity?
Access control
Going a step beyond capabilities, the requesting party of a vendor security review will want to identify exactly who has access to what information and understand the means by which they access that information. Be prepared to answer questions like:
- Is access to our systems and customer data required? If so, why—and who has access to this data?
- How do you handle sub-processors? Are they up to all the same security standards you have for yourself, and will our data be passed through any sub-processors?
- Who has privileged access (that is, administrative access) to production systems?
- How often are accounts and access privileges reviewed?
- Is MFA enforced for employees’ email accounts?
- Are all company-issued computers for employees fully disk-encrypted?
- What measures do you have in place to prevent unauthorized access to your systems from outside your company?
Policies, process, and documentation
This is the meat and potatoes of your vendor security review. While many of the certifications we talked about above will already answer these questions, some prospects will require policies and documentation above and beyond the required certifications.
Security reviewers may ask if you have:
- An Information Security Policy
- A Data Back-Up and Disaster Recovery Policy
- A Clear Desk and Clear Screen Policy
- Personnel screening and vetting standards (e.g., do you perform background checks on new hires?)
- Phishing training
- An Acceptable Use Policy for employees
- Confidentiality clauses in employment contracts (and quick enforcement of breaches of contract)
- Segmented customer data and environments
Disaster prevention and planning
You have your plans in place—but do your plans have plans for when things might go south? In practice, being over-prepared is table stakes when it comes to disaster prevention simply because of the sheer cost of a data breach.
Make sure you are prepared to answer the following:
- Do you conduct mock information security or cybersecurity events or simulated response exercises?
- Do you conduct regular technology reviews and audits?
- Is there a secondary data center available in case your primary data center is unavailable?
- Are regular network penetration tests conducted? If so, how often? What is the scope of the tests? And how are any security vulnerabilities uncovered during the test remediated?
- If there were to be an emergency security issue with your product, how do we contact you?
Incident histories
As a final note: Having prior incidents won’t necessarily be a dealbreaker, but dishonesty and a lack of transparency would be. If a breach has happened, be forthright about it and what steps you’ve taken to address it.
Best practices for passing risk assessments
Want to be the best possible partner during the security review process and close more deals faster? These best practices will help your sales organization get even more prepared for the vendor security review process:
1. Be informed and act professional
Put aside the checklist of things a vendor risk assessment will cover, and at its core, the security review is primarily about establishing trust. What foot do you want that relationship to start on?
If you enter the process of a risk assessment seeming annoyed, careless, or entitled to someone’s trust, you send a huge red flag.
Instead, project confidence in your security standards and an eager willingness to help make the reviewing party’s job as easy as possible.
And finally: When you are asked questions, do not lie. Seriously, don’t lie. Ever.
Don’t lie about your current state, even if you have plans to implement new security measures or employee policies in the near future. Information security officers at large enterprises will verify, and being dishonest will derail the whole process.
2. Understand where in the sales cycle your security review falls
You may project the deal is going to close in October, but didn’t account for a security review that may take several weeks to several months due to factors out of your control.
Knowing where it will fall in the sales cycle can help you make more accurate revenue forecasts.
If you’re working with a first-time or non-technical buyer, they also may not even realize they are going to have to ask for a security review from their IT team, so you can help educate and prepare them!
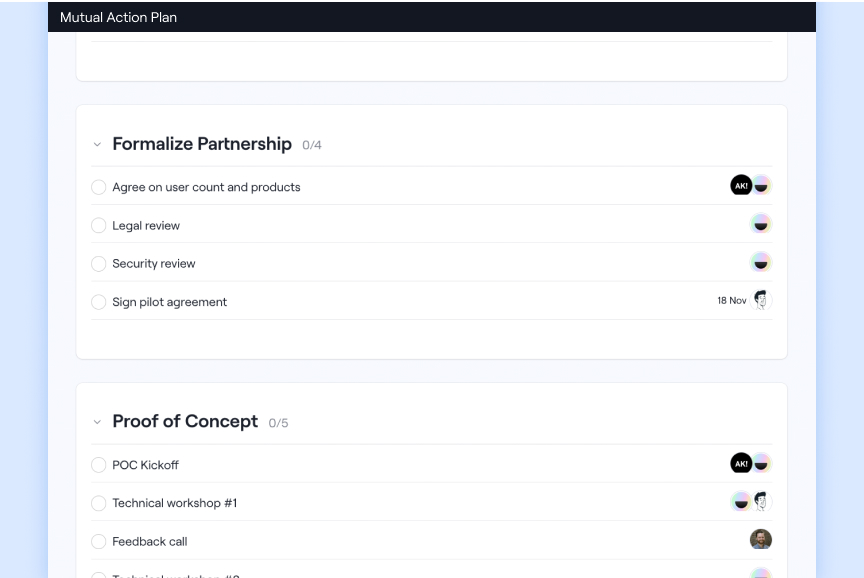
💡 Tip: Add the security review as a step in your mutual action plan so that your buyer knows it’s coming too.
3. Organize your documentation before you need it
What is within your control, though, is your own ability to get your ducks in a row before the security review requests ever start rolling in.
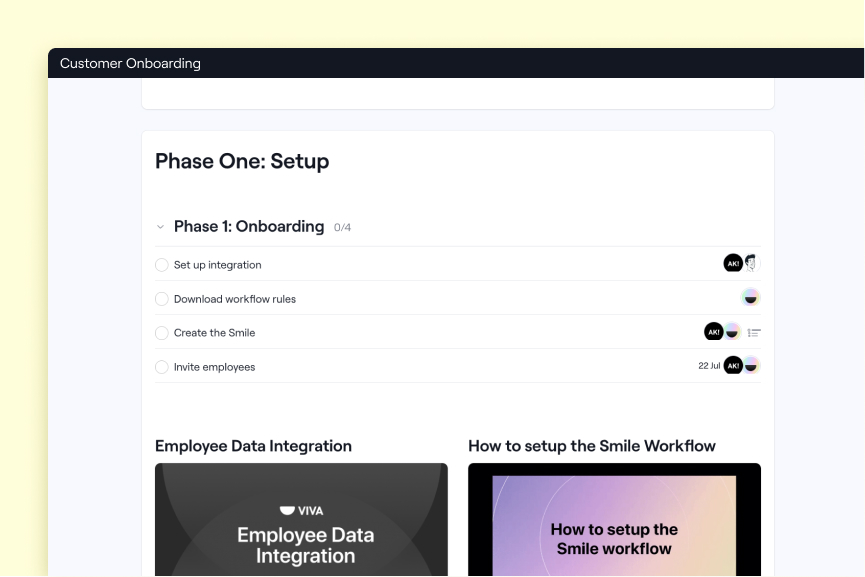
With Dock’s Security Profiles, you can do most of your risk assessment work ahead of time, allowing you to get it right once and then stay on top of it instead of starting from scratch with each deal:
- Quickly set up a security profile in Dock where your internal IT, legal, and security teams can upload credentials and compliance documents (and easily keep them up-to-date)
- When a prospect makes a security review request, Sales can simply add the security profile to the prospect’s Dock workspace
- Additionally, you can set up to-dos and action plans all within your Dock workspace to keep the review process moving along

Over time, you can update this hub with client FAQs and commonly requested info to reduce duplicate work and overall make it much less complex to manage vendor risk assessments during the sales process.
This creates standardized, synced security documentation that is always up-to-date—so when it’s time for a security review, you can simply drop the relevant info into your prospect’s workspace and accomplish in 2 hours what would normally take 2 weeks to track down. (You’ll also be IT and security’s best friend by giving them the lead time they need.)
4. Be proactive in sharing info and managing the relationship with the buyer
If you present your security info in advance to a prospect through a Dock workspace, you may also be able to avoid filling out huge spreadsheets or questionnaires from the client.
Much of a security review is a check-the-box exercise, so presenting information promptly and professionally before being asked takes the work off the plate of the reviewer, and creates a positive perception that your team has its stuff together.
Projecting yourself as trustworthy in this way is just as important as being buttoned up on the technical side. It shows that you are self-managing and will be easy to work with in the future.

5. Lean on your internal security team for additional best practices
Feeling lost in the process, or does it like technical terms are going over your head? This is totally normal.
Don’t be afraid to reach out to your own team (the ones responsible for evaluating the vendors your company uses) to ask all of your “dumb” questions ahead of time.
Your internal team can also help you understand the implications of recent security breaches in the news or recent updates to popular certifications so you can go into conversations informed.
They can also serve as a safe “test environment” (so to speak) for the first pass of your security review documentation before sending it over to the prospect.
You might try asking them, “If I were to submit this to you as the reviewing party, would you pass me—or would there be any red flags you would call out?”
Reduce friction in the security assessment process with Dock
Remember: the average security review adds four days to a sales cycle. Add up the four days required for each assessment—and multiply it by the dozens of inbound risk assessment requests IT and security teams have to respond to each month—and it’s clear you need to be extremely buttoned up in how you deal with vendor risk assessments.
But if you’re just relying on email chains and Slack threads to manage these requests, things are bound to fall through the cracks.
Stop scrambling to answer questionnaires, answering questions incorrectly, and not being compliant. It’s slowing down your sales cycle and causing you to lose deals.
Instead, use Dock’s Security Profiles to templatize and standardize your security review process so you can focus on building a strong relationship with your prospect.
Here's a quick demo of how to manage your company's security profile from the Dock backend:
Security Profiles are included for free with Dock Workspaces. You can create up to 5 Dock workspaces for free now with a free trial.




.png)




.png)